
DOWNLOAD
DATE
Contact
Blockchain is still a nascent technology — but it offers multiple advantages to businesses by introducing new business models and developing or revamping existing business models, all while reducing costs, enhancing security, and strengthening trust in ecosystems. Selecting the correct blockchain is critical. This Viewpoint helps you choose the right platform based on your business requirements. As a primer for your business decisions, we introduce you to the world of blockchain, what it is, how it works, its benefits, and the different options you should consider to best match your needs.
Blockchain technology is a breakthrough technological innovation. It is a special type of database that has redefined how digital transactions are verified and stored through the use of distributed ledger technology (DLT). In the simplest form, DLT refers to the approach of recording data and storing the same data across multiple locations. Transactions are not stored by a single party; rather, the entire transaction history is recorded by multiple entities (the distributed ledger).
The revolutionary aspect behind blockchain is that processes are not updated and validated by a single individual, but a community of members. Instead of one central party, each node (i.e., a computer that validates and keeps track of transactions) agrees on a “shared reality” and stores a history of every transaction that has ever taken place within the network. This agreement is called “consensus.” Importantly, because every single transaction that has ever taken place within the network is recorded and permanently stored at each and every node, it is impossible to change the ledger’s history or send the same transaction twice. Hence, participants of a blockchain network don’t need to “trust” each other — because no single user can cheat the whole system.
Blockchain technology is safe and robust; thus, it’s ideal for storing and processing sensitive information. It is particularly suitable for transactions between parties that need to be verifiable and permanent, such as contracts, ownership of intellectual property (IP), digital identity and credentials, and, of course, cryptocurrencies.
BASIC BUILDING BLOCK
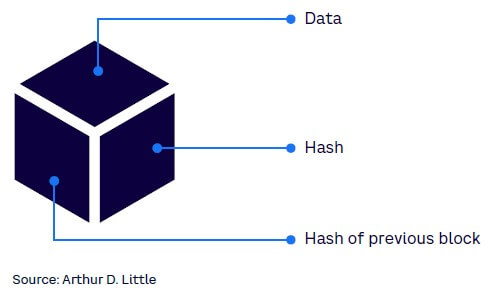
In a blockchain, transactions are stored in records, or blocks, linked together, with each newly generated block referring to the block before it with a unique identifying number called a “hash.” Figure 1 shows the three components of a block: data, hash, hash of previous block. These blocks constitute a chain; hence, the name “blockchain.” This chain continues on indefinitely.
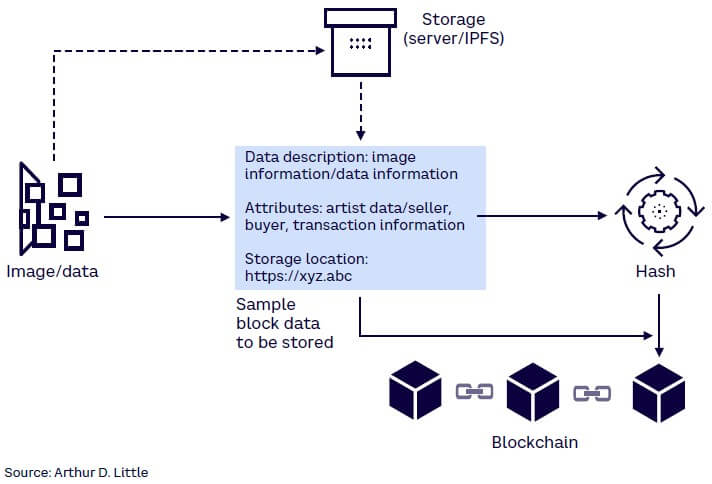
The amount of data you can store on a blockchain is limited as every node of the network stores a copy of the block. The data is typically either encrypted (for security reasons) or hashed to a fixed size that fits the block size limitations with the actual data stored on external servers (traditional or distributed databases) or by using distributed file systems like IPFS (InterPlanetary File System) — see Figure 2.
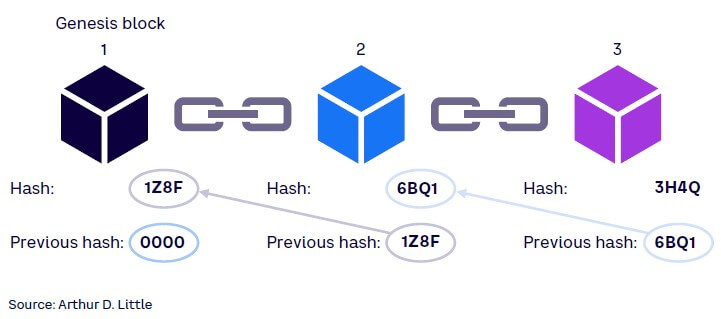
Hash, a mathematical function, is widely used in blockchain to protect the integrity and immutability of data stored on the distributed ledger. This function takes any size input data, performs calculations on it, and produces a fixed-sized output (hash). The hash function needs to ensure that no two inputs produce the same output (i.e., are collision-resistant). Hash functions are vital to protecting the immutability of the DLT. Thanks to hashing in the blockchain, each block added receives the previous hash (see Figure 3), and the new hash created is shared with all nodes. Each node maintains its own copy; anyone looking to modify one block will have to update the data across all nodes, making it exponentially harder as the number of nodes increase.
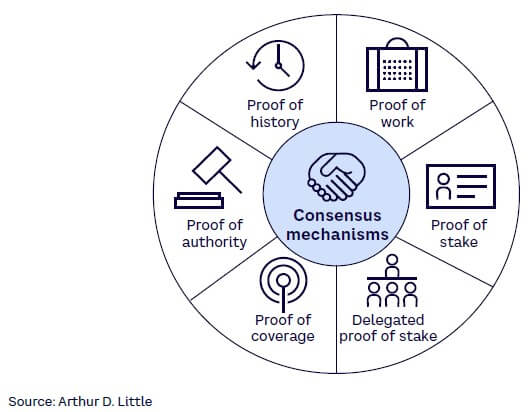
CONSENSUS MECHANISMS
Distributed systems — hence blockchains — need a mechanism to achieve synchronization and agreement between the network’s nodes to validate a transaction before it is added to the blockchain. Different blockchains use different consensus mechanisms and most are optimized for one or more but not all of the following: speed/throughput of transactions, energy consumption, decentralization, security, or scalability. Proof of work (PoW) and proof of stake (PoS) are the most popular consensus mechanisms from several options. Figure 4 highlights some of the new and most popular mechanisms:
-
Proof of work. PoW is the original consensus mechanism. It requires the solving of complicated mathematical problems, and only the first to solve the problem is rewarded. As there is only one winner per problem, miners (or nodes) compete to solve the puzzle first by investing significantly in processing power. Due to the large amount of processing power involved, it becomes impractical for any individual or group to meddle with a valuable cryptocurrency’s blockchain; hence, making it secure. On the flip side, since PoW is an energy-intensive process, it has difficulty scaling to accommodate vast numbers of transactions and may take a few minutes to validate/approve a transaction.
Use case: Bitcoin, the first and most popular cryptocurrency, uses PoW as its consensus mechanism.
-
Proof of stake. As the name suggests, nodes/validators stake capital (or crypto funds) as an incentive to validate network transactions and get rewarded for work. This is the most popular alternative to PoW due to its lower energy requirements and faster transaction speeds (~15+ transactions per second [TPS]). PoS maintains security because any rogue participant would need a majority stake (>51%), and any disruptions would work against that participant’s own interest. The drawback of PoS is that validators need to lock up a minimum amount of crypto for a certain period of time and will not be able to trade during this time.
Use case: As of this year, Etherium, the second-largest blockchain, has moved to PoS (from PoW) and is expected to reduce energy requirements by 99%. Flow, Polygon, and Cardano are other blockchains that have adopted PoS. NBA Top Shot powered by the Flow blockchain uses PoS to validate transactions.
-
Delegated proof of stake (DPoS). This is an enhanced version of PoS based on a voting system. Similar to PoS, nodes (i.e., voters) stake tokens to select block validators who in turn validate transactions. Block validators are rewarded for their work. Validators are constantly monitored and can be removed immediately if they act against the network’s interest. DPoS is more efficient and faster than PoS, delivering about 2,000-10,000 TPS. DPoS is more centralized than PoS in its validation, which enables it to be faster but also susceptible to cartelization/concentration of power and vulnerable to malicious activity.
Use case: Upland, a metaverse for players to buy, sell, and trade virtual properties, leverages the EOS blockchain to ensure transactions are recorded on an irreversible ledger.
-
Proof of coverage. PoC was introduced in the telecom industry. It is built on top of the Helium Consensus Protocol, which leverages the HoneyBadgerBFT consensus protocol, a consensus algorithm for asynchronous environments.
Use case: Helium, a decentralized wireless network for Internet of Things devices, is powered by cryptocurrency and described by Helium as “a physical wireless network that succeeds based on the amount of reliable coverage it can create for users deploying connected devices on it.” The network comprises devices called “Helium hotspots,” which are gadgets with antennas that can send small amounts of data over long distances using radio frequencies. The Helium blockchain uses PoC to authenticate a hotspot’s location. Per Helium, “PoC tries to verify, on an ongoing basis, that Hotspots are honestly representing their location and the wireless network coverage they are creating from that location…. [PoC] takes advantage of the unique, undeniable properties of radio frequency (RF) to produce proofs that are meaningful to the Helium Network and its participants.”
-
Proof of authority (PoA). PoA is very similar to PoS; instead of staking capital, a node’s identity is at stake. Here, blocks are validated by approved accounts or validators. This mechanism leverages a limited number of trusted validators, making this very scalable (50-2,000 TPS), since the time to gain consensus on a block reduces. This is ideal for private or consortium blockchains because the identity of the validator is revealed. The drawback of this mechanism is that authority is centralized to a few nodes. The right to validate is earned and expected to be secure as a node’s reputation is at stake and is expected to behave in the network’s best interest.
Use case: The R3 blockchain consortium along with 39 international financial companies have tested a KYC (know-your-customer) application using PoA over Microsoft Azure. Ronin network uses PoA, where Sky Mavis currently has the sole discretion around validators for its popular play-to-earning (P2E) video game Axie Infinity.
-
Proof of history (PoH). PoH is one of the newer consensus mechanisms. Typically, blocks are processed sequentially, and any new block will have to wait for conformation before being added to the blockchain. In PoH, each block receives a timestamp that lets the nodes know the order in which they were received; hence, the processing of a new block is not delayed.
Use case: Solana combines PoH along with PoS to create an extremely fast (~60,000 TPS) network. It uses PoS to validate the transactions produced by PoH.
There are numerous other consensus mechanism like proof of activity, proof of identify, proof of elapsed time, proof of capacity, Delegated Byzantine Fault Tolerance (dBFT), and Practical Byzantine Fault Tolerance (pBFT), to name a few. Upon selecting a consensus mechanism based on business need, companies will have to define who can run a node, along with validation requirements, roles and responsibilities, security policies, and so forth.
BRINGING IT ALL TOGETHER: HOW A BLOCKCHAIN WORKS
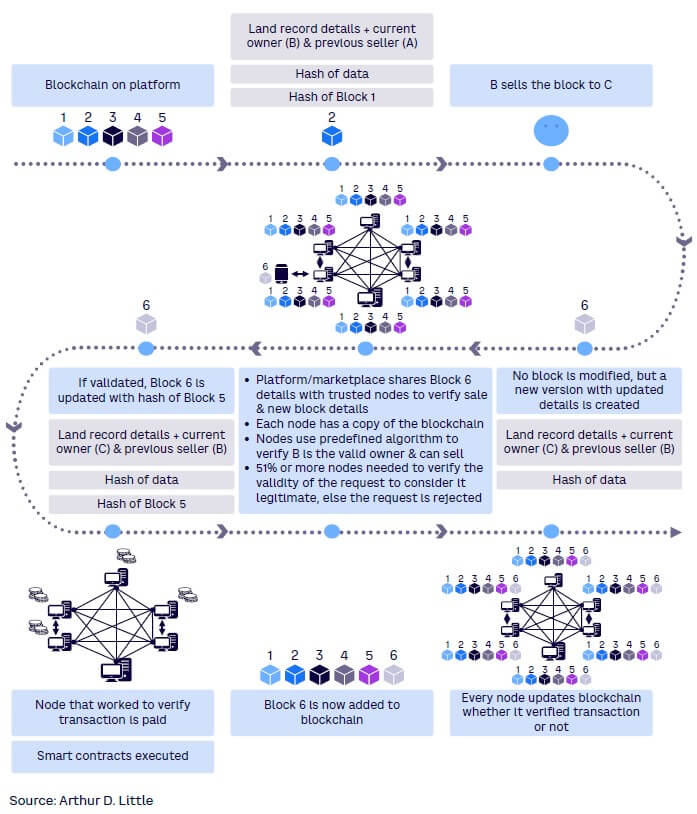
Blockchains are inherently decentralized (the control and decision making have moved from a centralized entity like an individual or organization to a dispersed network) and trustless (the network reaches consensus rather than a single authority) in nature. Figure 5 walks you through the steps a block goes through in adding a block and the decentralized and trustless nature of a blockchain.
SMART CONTRACTS: LOWER COSTS, ACCELERATE REVENUE
Smart contracts are programs stored on blockchains that are self-executing digital “if-then” statements between two or more parties (see Figure 6). When the groups’ terms are met, the contract is considered complete and executed automatically. Embedded in a blockchain, smart contracts are immutable and irreversible and provide various benefits, including speed, efficiency, accuracy, transparency, security, and financial savings.
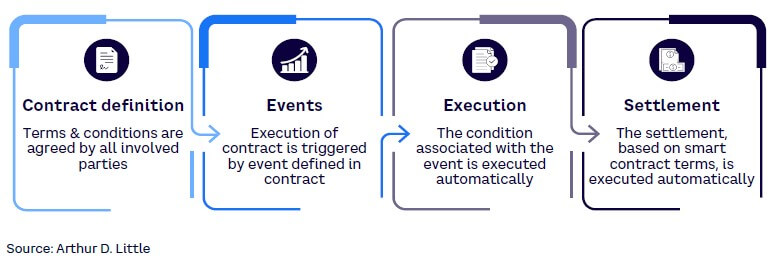
Smart contracts, being self-executing, are programed in a way that they can verify that the terms of the contract have been met and then execute the terms without the need of an intermediary or central authority. Hence, all participants can be certain of the outcome without the need of any mediator. Since a smart contract’s code is on a blockchain, anyone with access to the blockchain can inspect the code and verify the smart contract’s authenticity.
Telco impact: Improved efficiency through automation
Telecom carriers can leverage smart contracts (and blockchain) to automate many tasks and thus significantly improve efficiencies in many legacy systems. Many telco’s use multiple operational support systems (OSSs) and business support systems (BSSs) across different lines of businesses, especially with acquisitions. In addition, financial/market pressures have led telcos to typically underinvest in OSS and BSS platforms. Smart contracts can simplify/optimize and automate many of these processes, enabling different players in the ecosystem to transact directly with one another, prevent any disputes, and thus lower operational costs while making payment settlements instantaneous. This is just one of the ways blockchain can impact the telecom sector in the short term.
Media benefits: New business models & revenue streams
Blockchain forms the basic building block for many Web3 applications (see our recent Viewpoint “Web3 basics for telecoms & media”), and smart contracts can significantly alter the way media companies do business. Cryptocurrencies like Bitcoin and Ethereum support micropayments, which are impractical with classic payment mediums due to transfer costs. However, this capability, when combined with smart contracts, can support a new way of offering on-demand music services. In the music industry, for example, users can select the record of their choice and immediately remunerate all stakeholders with cryptocurrency.
Music isn’t the only industry that stands to gain from DLT innovation. All forms of digital media can leverage the benefits of blockchain by efficiently tracking IP ownership and streamlining fundraising and payout models. Blockchain technology can also significantly improve the digital advertising industry. Blockchain, as a system of record, along with smart contracts can provide an indisputable view on ad distribution and transactions and identify click discrepancies, bringing in accountability and transparency. This is just an example of one area of the media industry that blockchain will impact in the near future.
SELECTING THE RIGHT BLOCKCHAIN
There are two main categories of blockchain: permissionless (open to all) and permissioned (participation can be limited). Four options fit within those two categories, with some overlapping characteristics: public, private, consortium, and hybrid (see Figure 7).
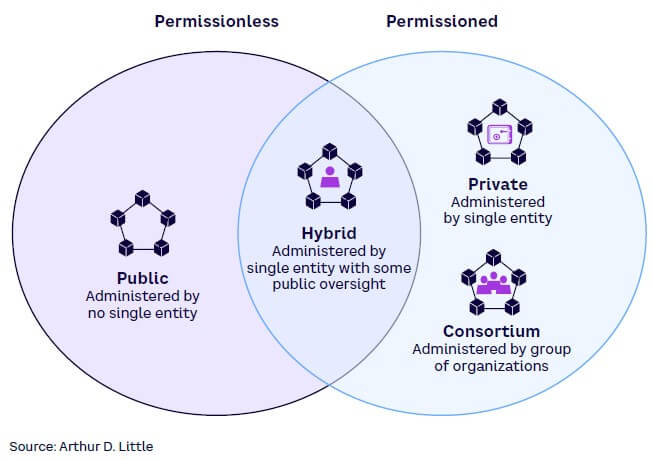
Public blockchains
Public blockchains are completely decentralized and permissionless, allowing anyone to join. With this aspect as its foundation, public blockchains offer equal rights to access and allow anyone to create new blocks and/or validate blocks of data. Heavy power consumption required to maintain DLT and the lack of complete privacy and anonymity are the primary disadvantages of a public blockchain. Since anyone can join a public blockchain, there is potential for malicious activities, such as hacking, token stealing, and network clogging.
Use case
The Helium blockchain is an “open source, public blockchain that incentivizes the creation of physical, decentralized wireless networks.” Instead of building out the network themselves, Helium pays individuals in its cryptocurrency, Helium Network Tokens (HNT), to operate hotspots, thus eliminating the complexity of building and maintaining the network.
Private blockchains
Private blockchains are permissioned blockchains where the owner determines the level of access to its network. Rules will be set and can be changed by the administrator. The control here sets up private blockchains as a great use case for companies or organizations that want the benefits of blockchain in a closed environment. Private blockchains tend to be faster and more secure as the owner/admin controls the nodes, allowing the consensus to be achieved faster.
Use case
R3, a consortium of some of the world’s biggest financial institutions, created an open source DLT platform called Corda. Corda is a private, secure DLT platform, designed for the financial industry. HSBC implemented R3’s Corda blockchain network on Google Cloud. HSBC used Corda for its custody blockchain platform Digital Vault, digitizing certain transaction records, which lowered client onboarding times from months to weeks.
Consortium blockchains
Consortium blockchains are also permissioned blockchains but differ from private blockchains as they are administered by a group of organizations. As a permissioned blockchain, the benefits of a consortium blockchain include control, security, speed, and scalability. The main drawback is that it needs agreement of all participants to implement any upgrades. The benefits of a consortium blockchain are similar to a private blockchain as access is controlled. Consortium blockchains enjoy more decentralization than private blockchains, resulting in higher levels of security.
Use case
we.trade is a blockchain-based trading platform founded by a consortium of banks in Europe. It connects buyers, sellers, and their banks in a network that uses the IBM Hyperledger private blockchain technology. It leverages DLT and smart contracts to help simplify international transactions.
Hybrid blockchains
As the name suggests, hybrid blockchains leverage the benefits of public and private blockchains. They are handled by a single organization that controls access to the network but also offer public blockchain features, such as integrity, transparency, and security, providing the best of both private and public blockchain solutions. This gives organizations better control over what they want to achieve rather than adjusting plans based on technology limitations.
Use case
XinFin is a hybrid blockchain built on both Ethereum, a public blockchain, and Quorum, a private blockchain. The hybrid network runs on a DPoS consensus mechanism. The network, as a public-state network, is shared by all members. A subset of members can share a private network for sensitive data.
Conclusion
THE NEXT STEPS
Blockchain can simplify business processes and lead to new opportunities and benefits through greater transparency, improved efficiency, enhanced security, and easier traceability. We recommend the following guidance to executives starting to evaluate blockchain technologies:
-
Telecom. Blockchain enables telecommunications companies an opportunity to automate processes, such as billing, roaming, and supply chain management. In the short term, the telecom industry should start deploying private blockchains for internal use cases and then open it to external customers. In the medium-to-long term, telcos can leverage blockchain platforms to enable higher-value use cases, such as identity management, data management, asset management, and revenue assurance, or even overlay network development.
-
Media. The media industry is well positioned to leverage the blockchain revolution as creators, consumers, and distributors stand to benefit from it. Besides enabling new revenue opportunities, blockchain technology enables greater personalized interaction between content creators and consumers. The industry should begin to evaluate blockchain technology for new business models and opportunities, especially around royalty-based micropayments and consumption-based pricing models.






